VPN vs. Zero Trust Network: Which is More Secure for Remote Access?
Zero trust fixes vulnerable trust models and limited visibility in VPNs by verifying all users and devices, encrypting everything, and monitoring all activity - before authorizing access.

In today's digital landscape, data breaches and cyberattacks are growing more sophisticated and prevalent. Traditional network security models centred around perimeter defences have proven insufficient to protect against modern threats. Zero trust networking has emerged as a new security paradigm to prevent data breaches and stop malicious actors.
But what exactly is zero-trust networking? How does it differ from technologies like VPN? And what are the main components required to implement zero trust architecture? First, let's understand "What is tunnelling?"

What is Tunneling?
Tunneling in networking refers to the process of encapsulating one network protocol or data packet within another protocol to ensure secure and efficient transmission of data across an interconnected network.
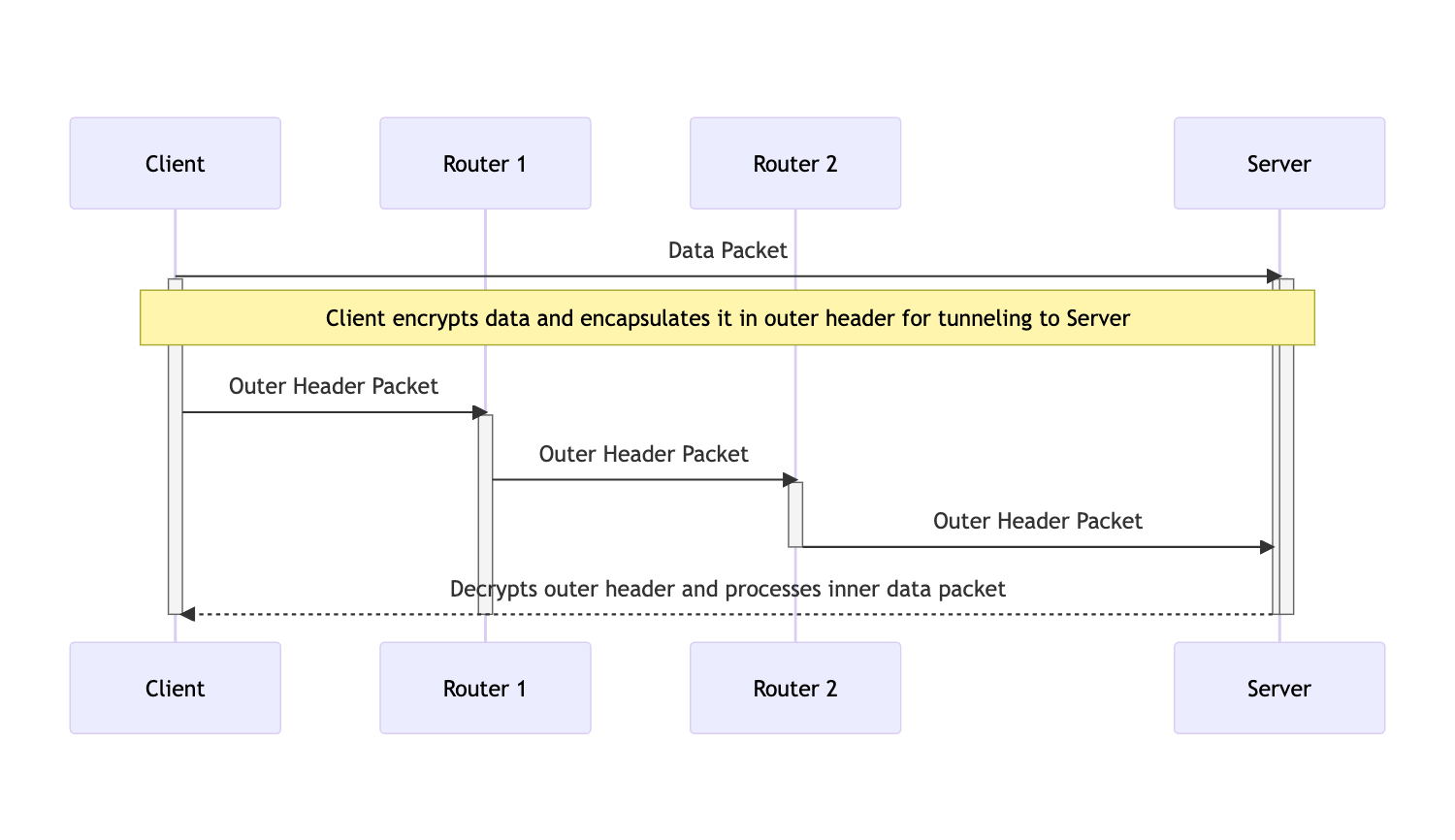
This technique is commonly used to extend private network communication over public networks, like the Internet while maintaining data integrity and confidentiality.
Tunneling Protocols:
- Virtual Private Network (VPN): VPNs use tunneling to create secure, encrypted connections over the internet. Protocols like IPsec and OpenVPN encapsulate data within encrypted tunnels to ensure privacy.
- Point-to-Point Tunneling Protocol (PPTP): PPTP is an older tunneling protocol primarily used for creating secure connections between remote users and corporate networks.
- Layer 2 Tunneling Protocol (L2TP): L2TP is often used in combination with IPsec to create secure tunnels for remote access or site-to-site connections.
- Secure Shell (SSH) Tunneling: SSH can be used for tunneling, allowing for secure connections to remote servers and port forwarding, ensuring data privacy.


What is a VPN?
A VPN (virtual private network) establishes an encrypted connection over a public network, allowing remote users to securely access private organizational networks and resources. It essentially extends an enterprise's private LAN across the internet to enable secure remote access.
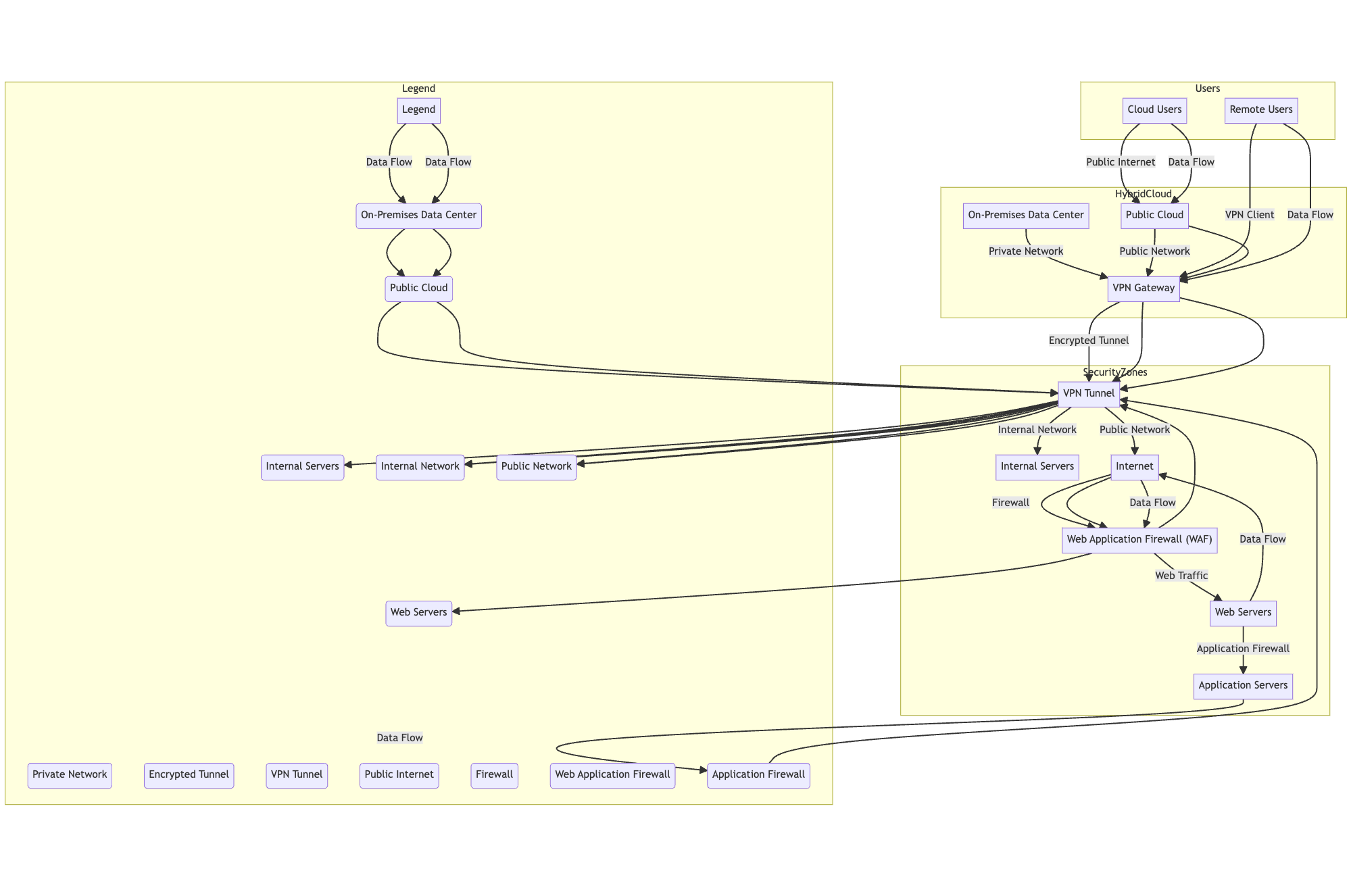
VPNs use tunnelling protocols like IPsec, SSL/TLS, or WireGuard to encapsulate and encrypt data for confidentiality. They rely on authentication mechanisms like passwords, tokens, or multi-factor authentication to verify user identities.
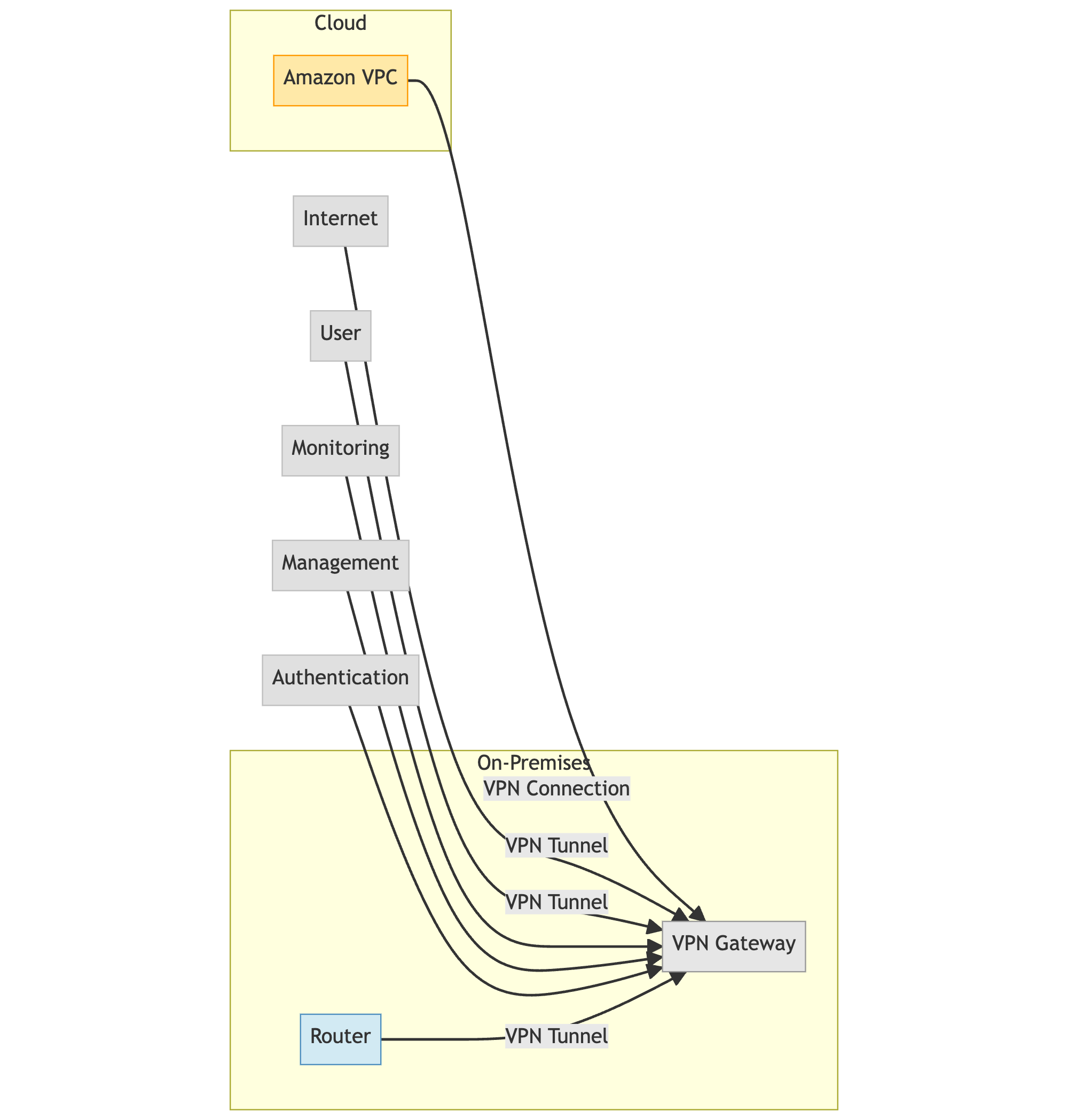
Once a remote user is authenticated to the VPN server, their device can access services, applications, and data within the organization's on-premise or cloud environment as if they were on the local network.
VPN Protocols and Technologies
Several standardized protocols and technologies provide the foundation for most VPN implementations:
- IPsec - Internet Protocol Security (IPsec) encrypts packets at the IP layer. Used for site-to-site VPNs.
- SSL/TLS - Secure Sockets Layer (SSL) and Transport Layer Security (TLS) operate at upper layers and are commonly used for remote access VPNs.
- WireGuard - An emerging VPN protocol focused on performance and ease of use. Offers modern cryptography compared to IPsec and TLS.
Leading enterprise VPN solutions include Cisco AnyConnect, Palo Alto Networks GlobalProtect, Citrix Gateway, Barracuda Networks, and others.
Limitations of VPN Security
While VPNs can securely enable remote access, traditional VPN technology has some security limitations:
A] Trust Model Weaknesses
VPNs are predicated on an inside vs. outside trust model. Once authenticated, remote users gain trusted access to all internal resources through the VPN tunnel. This broad implicit trust leaves internal systems vulnerable.
B] Perimeter-focused Approach
VPNs focus on securing the network perimeter and initial user authentication. However, they provide limited visibility into user activity or security events once inside the VPN tunnel.
C] Lack of Granular Controls
VPNs grant general network access rather than using context or attributes to define granular access privileges. Users are not restricted to only accessing specific necessary applications and resources.
These weaknesses make VPNs intrinsically vulnerable to insider threats, data exfiltration, and lateral movement following a breach.


What Exactly is a Zero Trust Network?
At its core, zero-trust networking operates on the principle of “never trust, always verify”. This model mandates that strict identity and access controls be applied to users, devices, networks and workloads - regardless of whether they reside inside or outside the network perimeter.
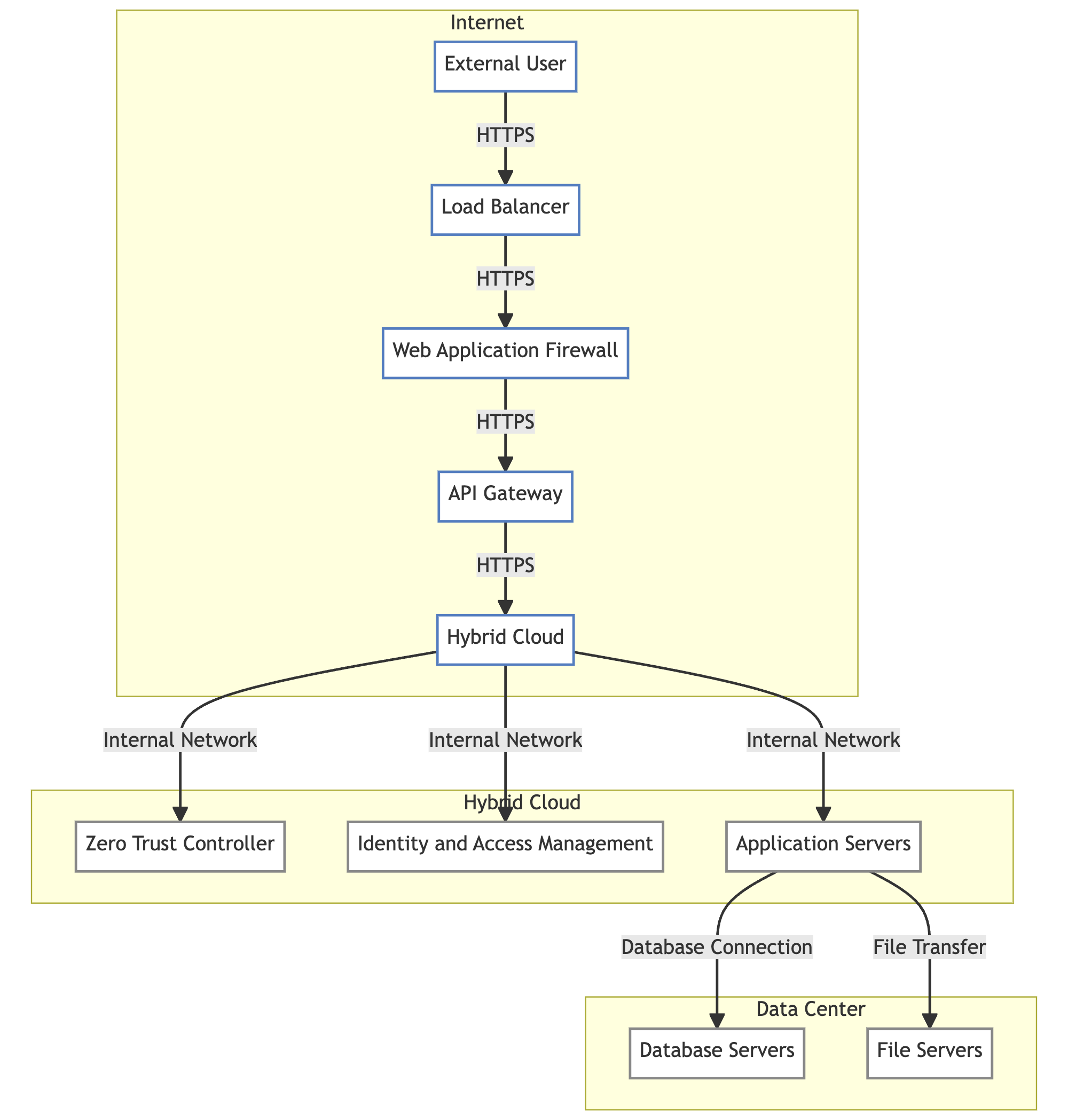
Unlike conventional network security approaches that focus on establishing a hard perimeter and implicitly trusting everything inside it, zero-trust architectures do not assume that any person, device or connection should be inherently trusted based on their location. Instead, zero trust dictates that all access requests must be authenticated, authorized, and continuously validated before granting zero-standing privileged access.
This shifts the focus from securing the perimeter to securing resources, data, and services using granular controls. By implementing zero-standing trust and comprehensive security monitoring, organizations can protect critical assets and minimize breach impact.
Capabilities of Zero Trust Architectures
- Multifactor authentication
- Endpoint security enforcement
- Software-defined perimeters
- Micro-segmentation
- End-to-end encryption
- Analytics for user and entity behaviour
Zero trust makes it far more difficult for attackers to penetrate defences and move laterally if compromised.
Core Principles and Concepts of Zero Trust Networks
There are several key philosophies and strategies that form the foundation of any zero-trust architecture:
- Least privilege access - Users and workloads are only provisioned the bare minimum levels of access needed to perform a specific function or task.
- Never trust, always verify - No users, systems or services are inherently trusted. Every access request must be authenticated and authorized based on context.
- Assume breach - Security is designed assuming a breach is inevitable. Controls focus on minimizing blast radius and preventing lateral movement.
- Micro-segmentation - Networks are divided into small, isolated segments or cells. This limits lateral movement following a breach.
- Continuous authentication - Users, devices and connections are authenticated, authorized and validated on an ongoing basis with appropriate frequencies.
- End-to-end encryption - Traffic is encrypted between microsegments and for all external connections to protect data.
With these principles in its architecture, zero-trust networks provide vastly superior security compared to legacy network security tools and topologies.


How Zero Trust Networking Differs from VPN Technology?
Many organizations looking to adopt zero-trust practices already have VPNs (virtual private networks) to allow remote users to connect securely to internal corporate resources.
Key Differences Between VPNs and Zero Trust Networks
While VPNs and zero trust aim to enable remote access securely, there are critical differences in their underlying philosophies and implementations:
- Trust model - VPNs connect remote users to a trusted internal network. Zero trust does not assume anything inside the perimeter is trusted.
- Access controls - VPN grants access to entire internal resources once connected. Zero trust uses dynamic, contextual access controls.
- Security posture - VPNs focus on the initial point of entry. Zero trust secures resources, users and devices.
- Verification - VPNs authenticate on initial connection. Zero trust re-verifies user and device credentials frequently.
- Monitoring - VPNs have limited visibility after access is granted. Zero trust implements continuous monitoring of all activity.
- Segmentation - VPNs allow access to the entire network. Zero trust micro-segment resources to limit movement.
While VPNs remain an important tool for remote access, zero trust principles allow organizations to securely embrace cloud and mobility by verifying all connections regardless of location.

Capabilities of a Zero Trust Architecture
Constructing an effective zero-trust network requires leveraging capabilities across users, devices, networks, workloads and data. Here are some of the key components needed:
#1. Granular Access Controls
- Multifactor authentication (MFA) - Strong authentication of user identity using factors like biometrics, tokens, etc.
- Single sign-on (SSO) - Allows secure access to multiple applications without reauthenticating.
- Role-based access controls - Assigns users only the permissions needed for their role.
- Attribute-based access controls (ABAC) - Defines fine-grained access policies based on specific attributes.
- Time-based controls - Restrict access to certain days/hours.
#2. Device Security
- Device compliance checks - Blocks access from compromised, vulnerable or unmanaged devices.
- Mobile device management (MDM) - Enforces security policies on end-user devices.
- Network access control (NAC) - Assesses device health before allowing network access.
#3. Micro-segmentation
- Software-defined perimeters (SDP) - Renders resources invisible until authenticated and authorized.
- Network segmentation - Breaks the network into smaller segments or cells to isolate critical resources.
#4. Monitoring & Analytics
- User and entity behaviour analytics (UEBA) - Uses machine learning to analyze behaviour patterns and detect threats.
- Security information and event management (SIEM) - Collects, aggregates and analyzes security event logs.
#5. Data Protection
- Encryption - Encrypts sensitive data both at rest and in transit.
- Tokenization - Substitutes sensitive data with non-sensitive tokens or aliases.
- Rights management - Controls usage of confidential documents.
With each of these key pillars, organizations can implement a true zero-trust program that secures access in a scalable, sustainable way across complex hybrid environments.
What do zero-trust implementations look like across various enterprise environments?
Zero trust deployments can vary significantly depending on specific organizational requirements and use cases. Here are some examples of real-world zero-trust implementations:
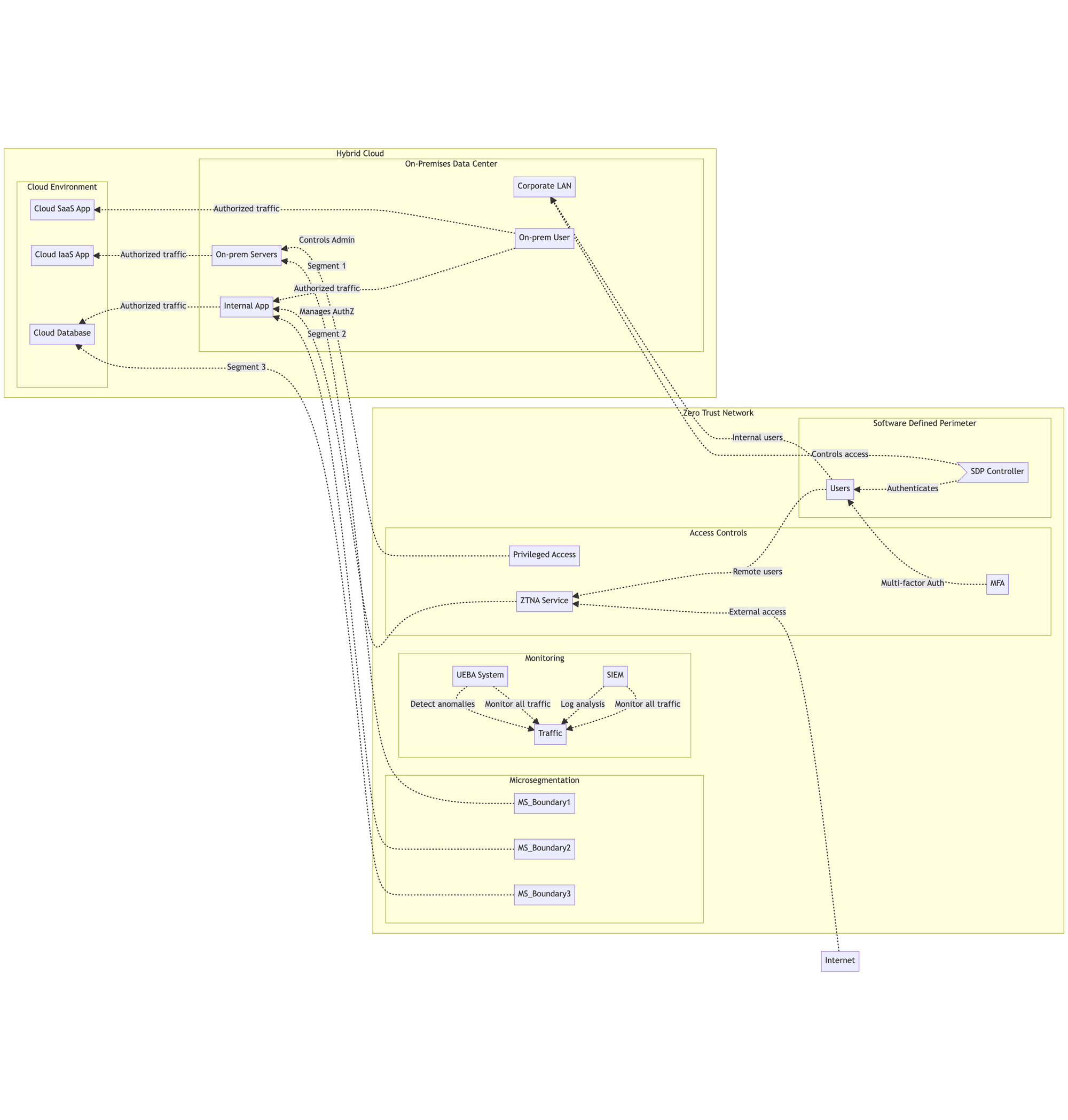
- Securing Enterprise Hybrid Cloud Environments
Many organizations adopt a zero-trust approach to secure access to workloads and data hosted across on-prem and multi-cloud environments. By treating all resources as untrusted, they can enable secure application access and mobility regardless of where apps and services are located.
Google utilizes zero trust principles built into its BeyondCorp enterprise security model to verify user and device credentials before allowing access to internal web apps from any location or device.
- Protecting Privileged Access
Government agencies and financial institutions enforce zero-standing trust principles for privileged users like system admins, remote workers, IT teams and third-party contractors.
Strict verification and least privilege controls are implemented to monitor all privileged sessions in real time and prevent insider threats.
- Adopting Zero Trust for Mergers and Acquisitions
During mergers, acquisitions or divestitures, zero trust models enable organizations to rapidly onboard and offboard users, devices and networks without inherent trust risks. Granular micro-segmentation also helps safely integrate networks.
Capital One was able to quickly migrate an acquired company’s systems by leveraging zero trust capabilities from Akamai rather than taking the traditional years-long perimeter security overhaul approach.

Challenges in Adopting Zero Trust Networks
While interest in zero trust architecture continues to accelerate, organizations need realistic expectations about the challenges involved in implementing:
#1. Overcoming Existing Assumptions About Trust
Zero trust represents a profound shift from conventional network security thinking. Moving from “trusted inside, untrusted outside” to a trust-none model requires major cultural and organizational change.
#2. Managing Increased Complexity
The layered controls and context-aware policies of zero-trust environments lead to higher complexity than implicit trust models. Orchestrating zero trust across hybrid technology stacks with legacy systems poses difficulties.
#3. Minimizing Impact on User Experience
More rigorous device posture checks and continuous re-authentication could negatively impact user experience. Performance may also suffer from decrypting/re-encrypting traffic at microsegment boundaries.
#4. Achieving Consistent Security Across Environments
Enforcing unified zero trust policies consistently across on-prem and multi-cloud environments with decentralized control can prove highly challenging.
Through extensive planning, pilot testing and a phased implementation approach, organizations can overcome these hurdles and transition to zero trust in a manageable, step-by-step manner.


The Future of Zero Trust Networks
By 2027, 80% of organizations expect to have zero trust either fully deployed or in the planning stages according to Enterprise Strategy Group research.
#1. Increasing Use of Artificial Intelligence and Machine Learning
Vendors are already applying AI and ML to improve threat detection, enable smarter adaptive access decisions, identify suspicious user activity, and optimize least privilege controls.
#2. Development of Zero Trust Policy Frameworks
Leading organizations are defining comprehensive zero-trust frameworks to align technical capabilities and policies to key objectives around securing data, people, devices and networks.
#3. Integration With Managed Security Service Providers
To supplement in-house staff, enterprises are leveraging Managed Zero Trust Providers for integrated expertise and service-based offerings designed around zero trust.
#4. Growing Focus on Zero Trust for Data Security
Organizations are increasingly adopting zero-trust principles focused on protecting critical data and workloads. Data-centric frameworks like the NIST Zero Trust Architecture model are emerging.
As zero trust architecture evolves from early adoption to mainstream implementation, it will continue to drive the next generation of enterprise security programs - enabling digital innovation and Business 4.0 transformation securely.
Conclusion
In conclusion, while VPN technology has securely enabled remote network access for many years, zero-trust networking represents a more robust and adaptive approach tailored for today's cloud-centric world. By moving beyond implicit trust models and implementing continuous verification of users and devices based on context, zero-trust architectures provide vastly superior protections for critical business applications and data in modern hybrid environments.
Core zero trust principles like least privilege access, ubiquitous encryption, and user behaviour monitoring help stop malicious actors and insider threats. And capabilities like multifactor authentication, software-defined microsegmentation and granular access controls give organizations the visibility and control needed to prevent unauthorized access.
Summary
- VPNs and zero-trust networks both aim to provide secure remote access to private enterprise resources.
- However, VPNs have intrinsic vulnerabilities due to: perimeter-focused trust models, lack of granular controls after initial login, and limited monitoring capabilities.
- Zero trust networking overcomes these issues using identity and context to drive dynamic, least privilege access decisions and implementing continuous security monitoring.
- Leading organizations are gradually shifting from legacy VPNs to zero trust architecture to enable more adaptive security in the cloud era and better safeguard critical digital assets.
By transitioning to a zero-trust strategy over time, enterprises can confidently embrace mobility, cloud and digital transformation with end-to-end protection rather than just a hard perimeter.

FAQs
Is Zero Trust Networking suitable for small businesses, or is it primarily for large enterprises?
Zero Trust Networking principles can benefit organizations of all sizes. Small businesses can implement aspects of ZTN to enhance their security posture.
How does Zero Trust Networking handle user privacy and data protection?
ZTN prioritizes user privacy and data protection by strictly controlling access and continuously monitoring for potential threats.
What are some common misconceptions about Zero Trust Networking?
One common misconception is that ZTN is too complex or costly to implement. In reality, organizations can tailor ZTN to their specific needs and budget.
What are the main vulnerabilities in VPNs?
Key issues with VPNs involve the broad implicit trust granted to authenticated users, lack of granular controls, and limited monitoring once inside the VPN tunnel.
Does zero trust completely replace VPN technology?
Potentially over time, but most implementations leverage VPN capabilities during initial phases focused on MFA and device security.
What are the main components of a zero-trust architecture?
Core components include multifactor authentication, endpoint security, micro-segmentation, encryption, analytics and zero-trust network access controls.
What are examples of zero-trust network access solutions?
Leading zero-trust network access vendors include Zscaler, Cloudflare, Akamai, Perimeter81, Appgate, and others.

