What is FIDO? — The Future of Secure and Passwordless Authentication
Say goodbye to passwords! FIDO is a complex and strong system that is based on public and private keys, and it improves both usability and security.

You know what I hate, I mean hate? Passwords. There are just too many of them, and they're so hard to keep up with. I find myself losing them all the time. I bet you feel the same way. Well, what if I told you there's a way to ditch these passwords without compromising security? There's a way that not only eliminates the hassle but also enhances the usability of the system while making it more secure. Achieving both of these at the same time is quite a feat.
You may have heard about "Passkeys". Passkeys provide an easy, secure single sign-on solution by using technologies like biometrics and device-bound cryptography. Passkeys are an implementation of FIDO’s public key cryptography concepts that extend their ease of use even further...
What is FIDO?
FIDO (Fast Identity Online) is an authentication protocol that enables users to securely log into online services and applications without the need for passwords. Instead, it uses cryptographic key pairs to verify user identities.
FIDO is designed to be compatible with existing web browsers and platforms and to work with any type of authentication service or identity provider. FIDO is widely adopted by many websites and applications that offer FIDO as an option for their users. Some examples are Google, Facebook, Dropbox, GitHub, Microsoft, PayPal, eBay, and many others.
😑 The Actual Problem with Passwords
Passwords have long been the standard for authentication online. However, they have major weaknesses:
- They are hard to remember, so users often choose weak, easy-to-guess passwords.
- People reuse the same passwords across many sites.
- Passwords can be easily stolen through phishing attacks or data breaches.
This makes password-based authentication insecure, inconvenient, and a major security liability.

How Does FIDO Work?
FIDO provides an alternative approach using public-key cryptography. Here's a high-level overview:
FIDO consists of two specifications:
FIDO Universal Second Factor (U2F) and FIDO Universal Authentication Framework (UAF). FIDO U2F is a protocol that allows users to authenticate themselves with a simple tap of a physical device that contains a FIDO key.
For example, a user can log in to a website by entering their username and tapping a USB token or a smartphone that supports FIDO U2F. FIDO UAF is a protocol that allows users to authenticate themselves with a biometric factor or a PIN that unlocks a FIDO key stored on their device. In other words, a user can log in to an application by scanning their fingerprint or entering a PIN on their smartphone that supports FIDO UAF.
Key Pairs and Registration
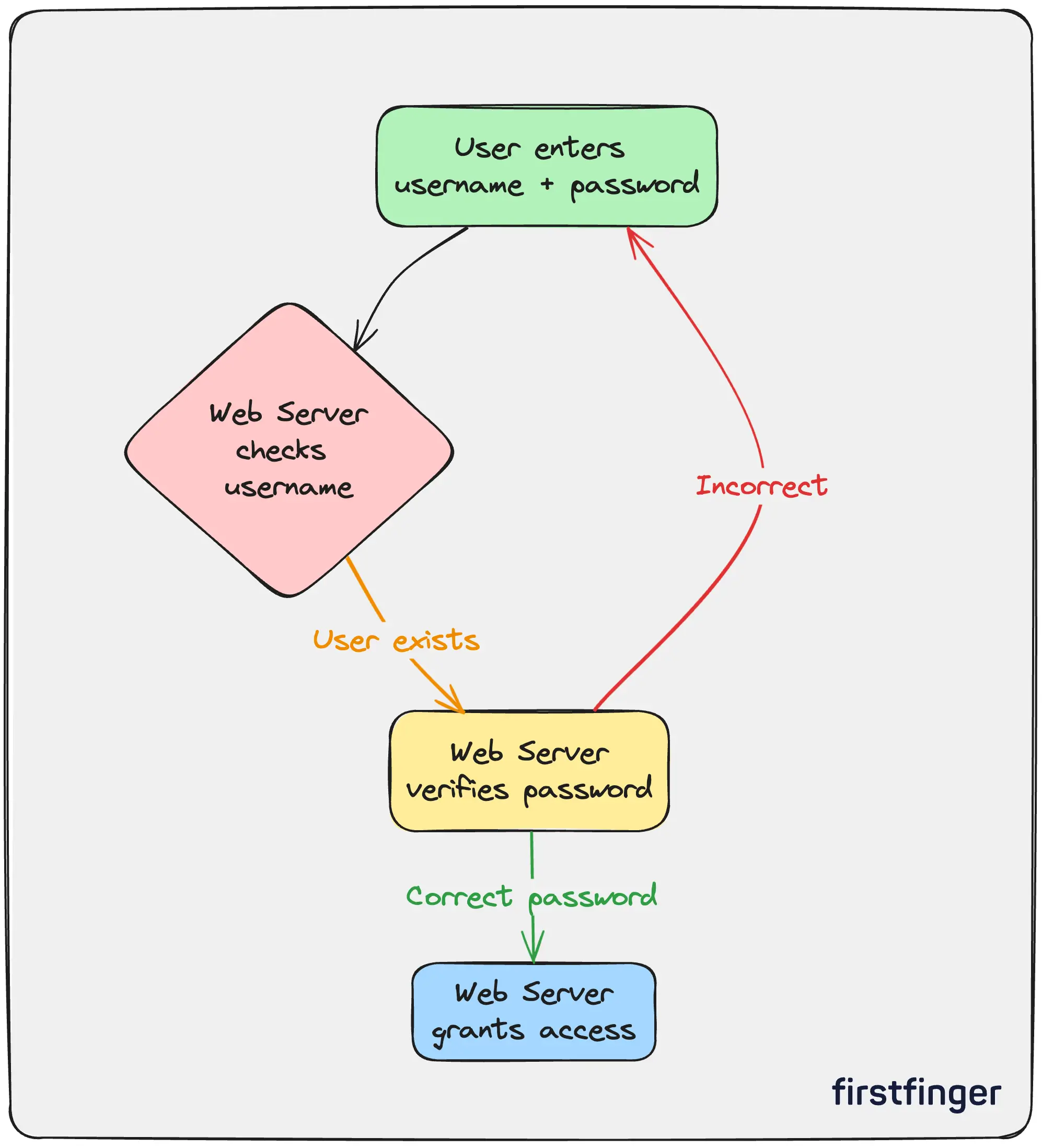
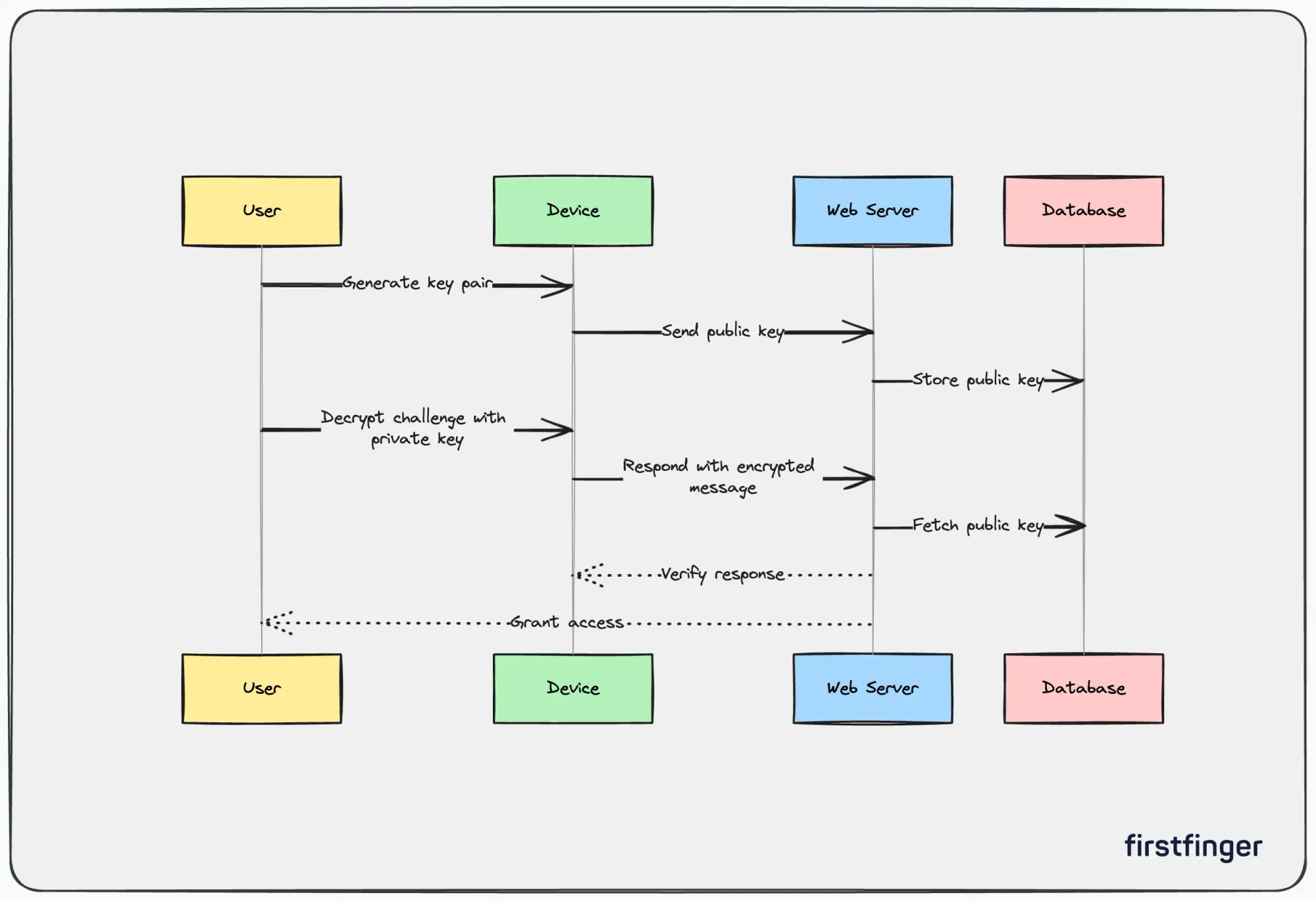
During registration with a site:
- The user's device generates a public-private key pair.
- The private key never leaves the user's device.
- The public key is shared with the site's servers.
- The site associates the user's account with their public key.
Cryptographic Challenges
When logging in later:
- The site issues a cryptographic challenge encrypted with the user's public key.
- The user decrypts the challenge with their private key.
- The user provides a response encrypted with their private key.
- The site verifies the response using the public key.
This allows the site to authenticate without any passwords changing hands.
FIDO Protocols
The FIDO Alliance was founded in 2012. There are two main protocol standards developed under the FIDO alliance for passwordless authentication:
FIDO U2F
FIDO U2F (Universal 2nd Factor) was the first protocol standard released in 2014. It enables the use of secure physical devices like USB security keys as a second authentication factor. The private key is stored on the physical device rather than the user's computer or mobile device. Inserting the key activates the local private key to authenticate.
FIDO2 - The Updated Version
FIDO2 was later introduced to expand and improve on FIDO U2F:
- Platform support - Expands beyond USB devices to platform-based authenticators like mobile device biometrics or built-in security chips like the TPM in many PCs. This improves availability and convenience.
- Client-side public key generation - The client device generates and stores public-private key pairs locally rather than relying on an external server. This enhances privacy.
- Single-factor support - Allows FIDO2 authentication to be used for single-factor primary authentication in some cases, offering an easier transition from legacy passwords.

Backwards Compatibility
An important benefit of FIDO2 over earlier protocols is it depends on backwards compatibility with existing sites using U2F. FIDO2 support can be added to existing infrastructure without breaking existing security key-based login. This facilitates an easier pathway for organizations to upgrade and transition to passwordless systems.
FIDO Supports Multi-Factor Authentication
FIDO also supports multi-factor authentication using:
- Biometrics like fingerprints or face recognition
- Hardware tokens, like a USB security key
The user's private key is stored securely and can only be accessed after biometric or hardware authentication. This further strengthens security.
Benefits of using FIDO
FIDO authentication brings major security and convenience benefits:
- No passwords: eliminate insecure passwords
- Phishing resistance: no credentials for attackers to steal
- Stronger authentication leverages hardware and biometrics.
- Ease of use: automatic and seamless for users
- Resists replay attacks; relies on cryptographic challenges
More & More Tech Giants Adopting FIDO
In short, FIDO can eliminate passwords and replace them with cryptographic keys that are unique for each website or application, FIDO protects users from common cyberattacks and reduces the burden of remembering and managing passwords.
The FIDO alliance includes over 250 leading technology companies. Major websites like Google, Facebook, and Twitter support FIDO authentication. Support is growing across industries to replace passwords with stronger FIDO authentication.



